Natural disasters often bring out the best in people, with communities and organizations coming together to help those in need. Unfortunately, they also present opportunities for cybercriminals looking to exploit the chaos for financial gain. With Hurricane Helene and other recent hurricanes affecting Florida, Veriti’s research team has identified several emerging cyber threats targeting vulnerable individuals and organizations. Three key emerging threats: FEMA claim scamming, phishing attacks using hurricane-related domains, and malicious activity disguised as FEMA-related files.
FEMA Claim Scamming
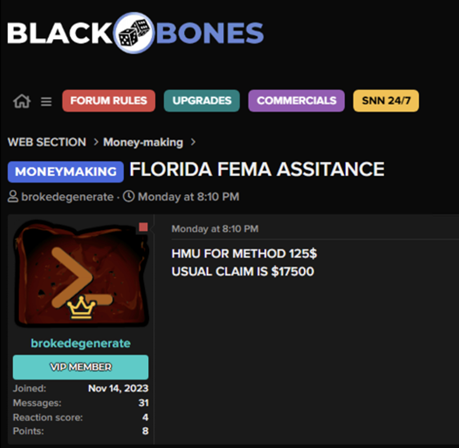
One of the first major threats we observed is FEMA claim scamming, where cybercriminals pose as legitimate FEMA assistance providers to steal personal information and funds. A VIP member on a hackers forum, under the alias “brokedegenerate,” recently posted about a new scam targeting Florida residents affected by the hurricane.
On the forum, the scammer shares tactics for creating fake FEMA assistance claims, with detailed instructions on how to deceive victims and siphon off funds intended for disaster relief. This kind of scam is particularly dangerous, as victims are already in a vulnerable position due to the natural disaster.
Forum post: https://blackbones.net/threads/florida-fema-assitance.15340/
Phishing Campaigns Targeting Hurricane Victims
In addition to FEMA claim scams, we’ve observed a surge in phishing domains registered to exploit the hurricane and relief efforts. These domains are designed to trick individuals into providing personal information, such as Social Security numbers, credit card details, and other sensitive data.
Here are a few newly registered domains our team identified, which could be used for phishing campaigns:
- hurricane-helene-relief.com
- hurricanehelenerelief.com
By using hurricane-related terms and associating themselves with disaster relief, these domains aim to create a sense of urgency, making it more likely that victims will fall for the phishing schemes. Attackers will likely send phishing emails directing recipients to these websites, claiming to offer relief services or grant applications. Once victims input their personal details, the attackers can use or sell the data for financial gain.
Malicious Files Disguised as FEMA Documents
Cybercriminals are also using malicious files disguised as legitimate FEMA documents to distribute malware. A few days ago, a file named fema_grants_manager_user_manual.pdf was uploaded for virus scanning. Upon inspection, it was found to contain malicious content. Link to VirusTotal here.
The document appears to be a legitimate FEMA manual related to disaster recovery grants, referencing systems like the Grants Portal and Grants Manager, which are used to streamline the grant application process. However, the file includes a malicious payload that redirects users to a suspicious URL: zuwudijalekufas.mofien.co./za
Although we haven’t yet observed active infections from this campaign, the file’s existence highlights the potential for cybercriminals to use disaster relief programs as a cover for malicious activity.
Recommendations to Stay Safe
- Verify the legitimacy of relief efforts: If you or your organization are involved in disaster recovery, always verify that any communication related to FEMA or disaster assistance is coming from official sources. Double-check URLs, email addresses, and other indicators before sharing sensitive information.
- Be cautious of unsolicited emails and attachments
- Cybercriminals often use phishing emails to trick victims into downloading malicious attachments or clicking on dangerous links. If you receive an email with an attachment claiming to be from FEMA, verify its authenticity before opening it.
- Use up-to-date antivirus software
- Ensure your security software is updated regularly to detect and block malicious files and phishing attempts. Advanced endpoint detection and response (EDR) solutions can provide an added layer of protection.
- Educate your team
- Make sure that employees and volunteers involved in disaster relief efforts are trained to recognize phishing attempts and other cyber threats. Providing regular cybersecurity awareness training can help reduce the risk of falling victim to these scams.
As natural disasters like Hurricane Helene affect communities, it’s critical to remain vigilant about the cyber threats that follow in their wake.




