As the echoes of a 2023 fade, there’s barely a moment to catch our breath. 2024 has dawned with a brisk reminder: in the realm of cybersecurity, there is no rest for the weary. The new year greets us not with respite but with yet again, a fresh set of challenges as cyber attackers continually evolve, exploiting security gaps with relentless zeal. In this unceasing game of cat and mouse, the recent discovery of CVE-2024-0252 serves as a stark reminder – we must remain ever vigilant, for the cyber adversaries never sleep, and neither should we.
The CVE-2024-0252 Vulnerability: A ManageEngine Weak Spot
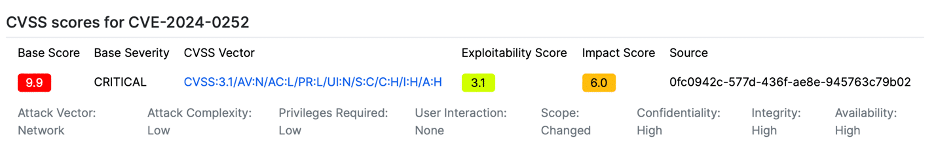
CVE-2024-0252 opens a dangerous door for attackers, allowing authenticated users to execute remote code on systems where ADSelfService Plus is installed.
CVE-2024-0252 exposes a flaw in this software that could be exploited by someone who already has a certain level of access (authenticated user). Specifically, it allows them to execute remote code on the system running ADSelfService Plus, opening up avenues for more significant security breaches. For instance, an attacker exploiting this flaw could potentially gain deeper access into the organization’s network, compromise sensitive data, or disrupt critical IT systems.
What is ManageEngine ADSelfService Plus?
Mythic Platform Misuse: A Double-Edged Sword
During our analysis, we discovered an alarming connection between the malware sample and the Mythic platform. Mythic, known for its collaborative and intuitive interface for red teaming, is built using GoLang, Docker, and Docker-compose. While designed for legitimate cybersecurity testing, its ease of use has, unfortunately, attracted malicious actors. This trend of repurposing security tools for malevolent objectives is a growing concern, blurring the lines between safeguarding and exploiting vulnerabilities.
The sample can be further inspected here

A Deep Dive into the Malware’s Tactics
The sophistication of this malware sample is evident in its use of advanced tactics and techniques. Analyzing the sample, available on VirusTotal, reveals the complexity of its design, including obfuscation and evasion strategies. The malware utilizes a range of methods mapped in the MITRE ATT&CK framework, such as Native API Execution, Obfuscated Files or Information, and System Network Configuration Discovery.
| Execution | ||||
| ATT&CK ID | Name | Tactics | Description | |
| T1106 | Native API | Execution | Adversaries may interact with the native OS application programming interface (API) to execute behaviors. Learn more | |
| Defense Evasion | ||||
| ATT&CK ID | Name | Tactics | Description | |
| T1027 | Obfuscated Files or Information | Defense Evasion | Adversaries may attempt to make an executable or file difficult to discover or analyze by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit. Learn more | |
| T1497 | Virtualization/Sandbox Evasion | Defense Evasion | Adversaries may employ various means to detect and avoid virtualization and analysis environments. Learn more | |
| Discovery | ||||
| T1140 | Deobfuscate/Decode Files or Information | Defense Evasion | Adversaries may use Obfuscated Files or Information to hide artifacts of an intrusion from analysis. Learn more | |
| T1480 | Execution Guardrails | Defense Evasion | Adversaries may use execution guardrails to constrain execution or actions based on adversary supplied and environment specific conditions that are expected to be present on the target. Learn more | |
| Discovery | ||||
| ATT&CK ID | Name | Tactics | Description | |
| T1016 | System Network Configuration Discovery | Discovery | Adversaries may look for details about the network configuration and settings, such as IP and/or MAC addresses, of systems they access or through information discovery of remote systems. Learn more | |
| T1083 | File and Directory Discovery | Discovery | Adversaries may enumerate files and directories or may search in specific locations of a host or network share for certain information within a file system. Learn more | |
| T1049 | System Network Connections Discovery | Discovery | Adversaries may attempt to get a listing of network connections to or from the compromised system they are currently accessing or from remote systems by querying for information over the network. Learn more | |
| T1497 | Virtualization/Sandbox Evasion | Defense Evasion | Adversaries may employ various means to detect and avoid virtualization and analysis environments. Learn more | |
| Discovery | ||||
| Command and Control | ||||
| ATT&CK ID | Name | Tactics | Description | |
| T1071 | Application Layer Protocol | Command and Control | Adversaries may communicate using OSI application layer protocols to avoid detection/network filtering by blending in with existing traffic. Learn more | |
| T1095 | Non-Application Layer Protocol | Command and Control | Adversaries may use an OSI non-application layer protocol for communication between host and C2 server or among infected hosts within a network. Learn more | |
| T1573.001 | Symmetric Cryptography | Command and Control | Adversaries may employ a known symmetric encryption algorithm to conceal command and control traffic rather than relying on any inherent protections provided by a communication protocol. Learn more [MG1] | |
The Prevalence and Impact
The prevalence of CVE-2024-0252 is not just a theoretical concern but a real-world threat. The statistics on exposed servers and the vulnerability’s exploitation rate emphasize the urgency for organizations to reassess their exposure and fortify their defenses. For a comprehensive understanding of the threat landscape and timely patching recommendations, CISA’s vulnerability summary offers invaluable insights (CISA).
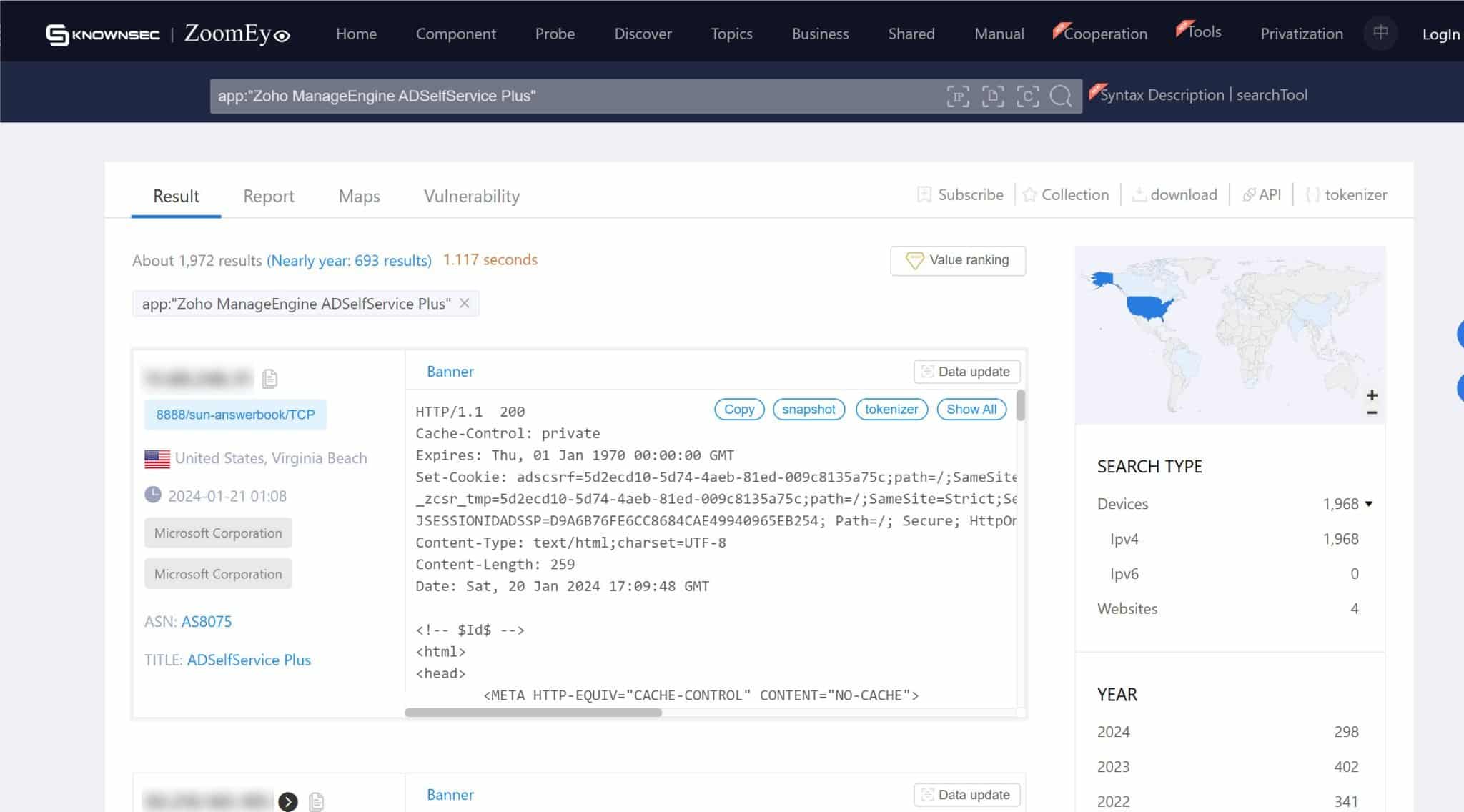
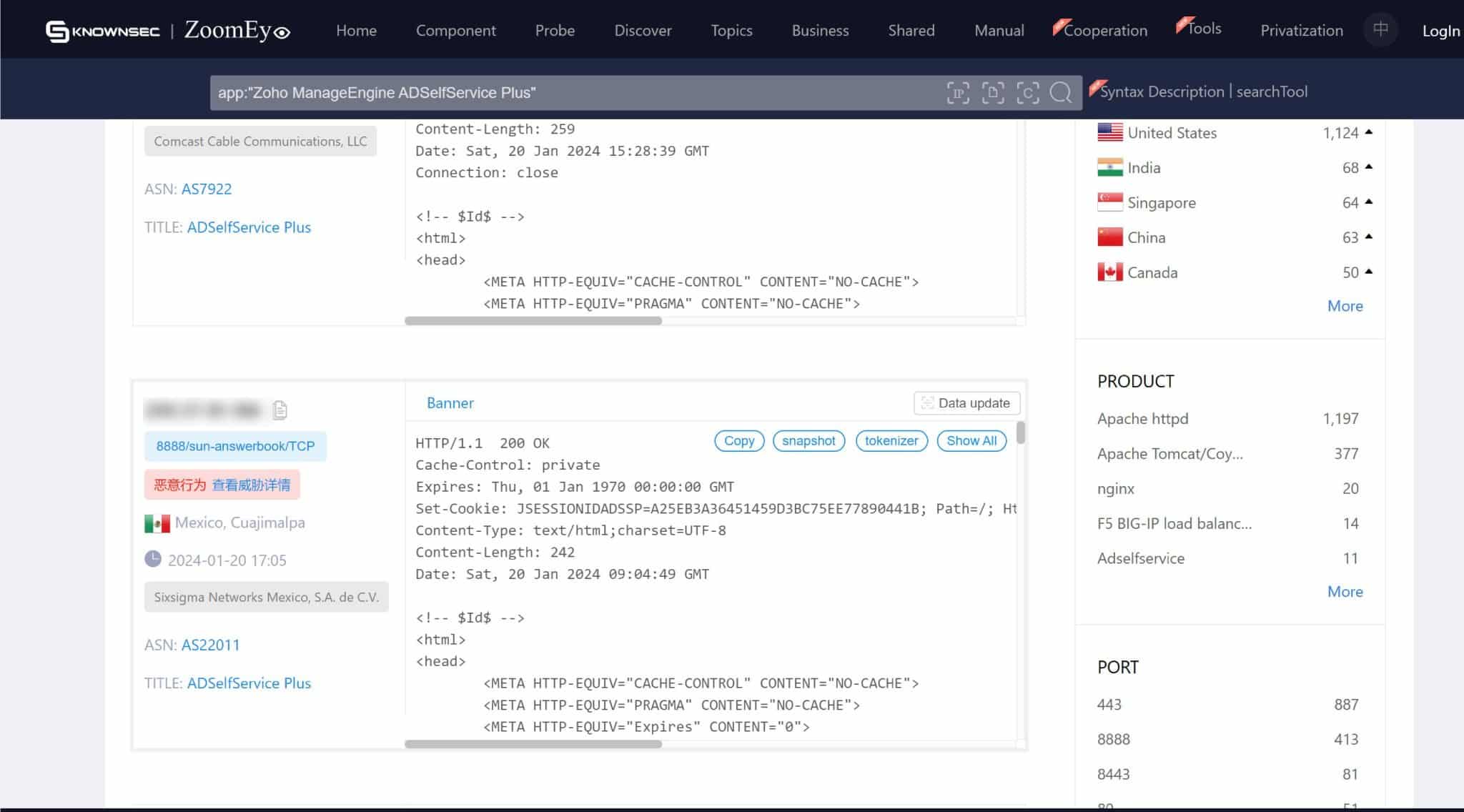
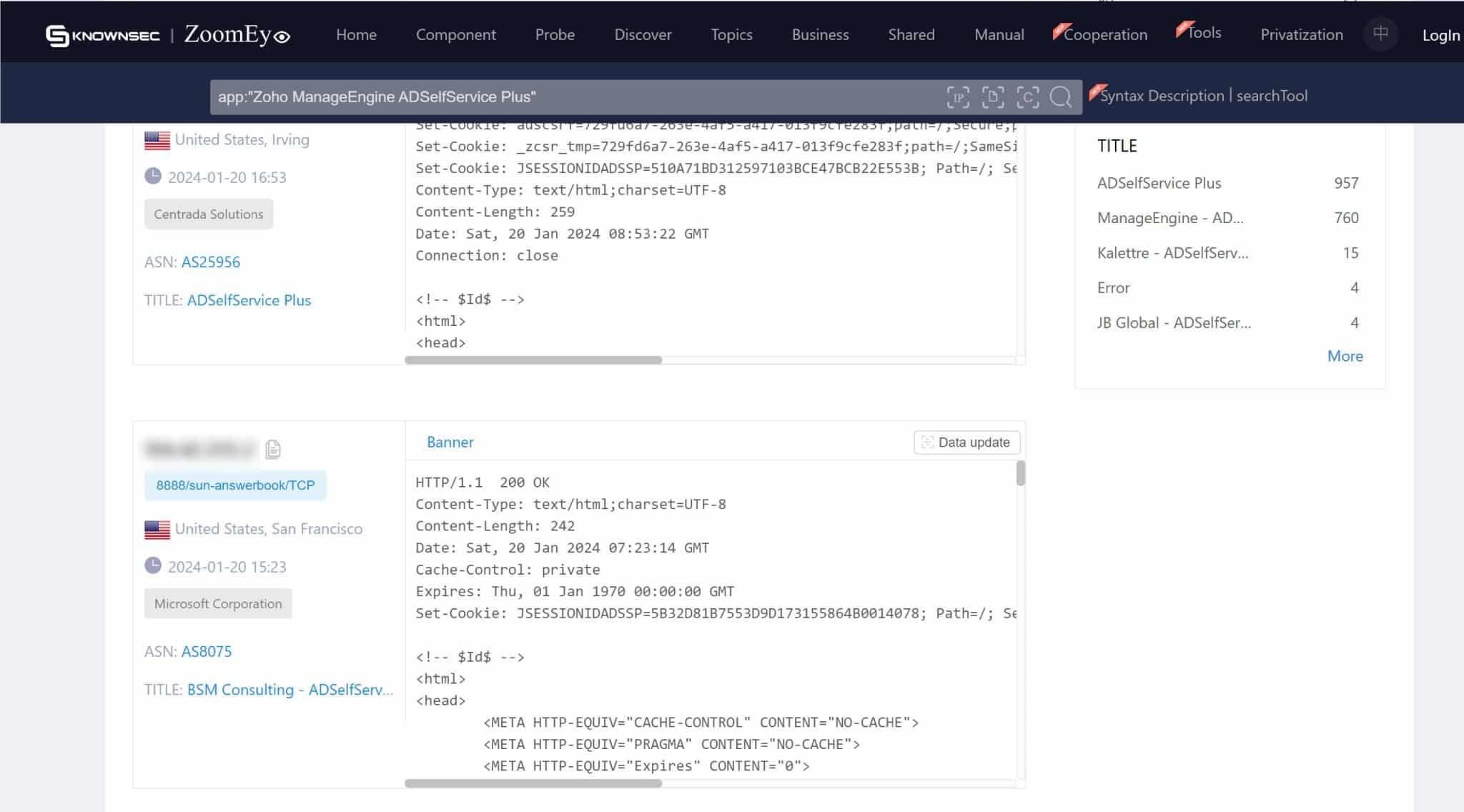
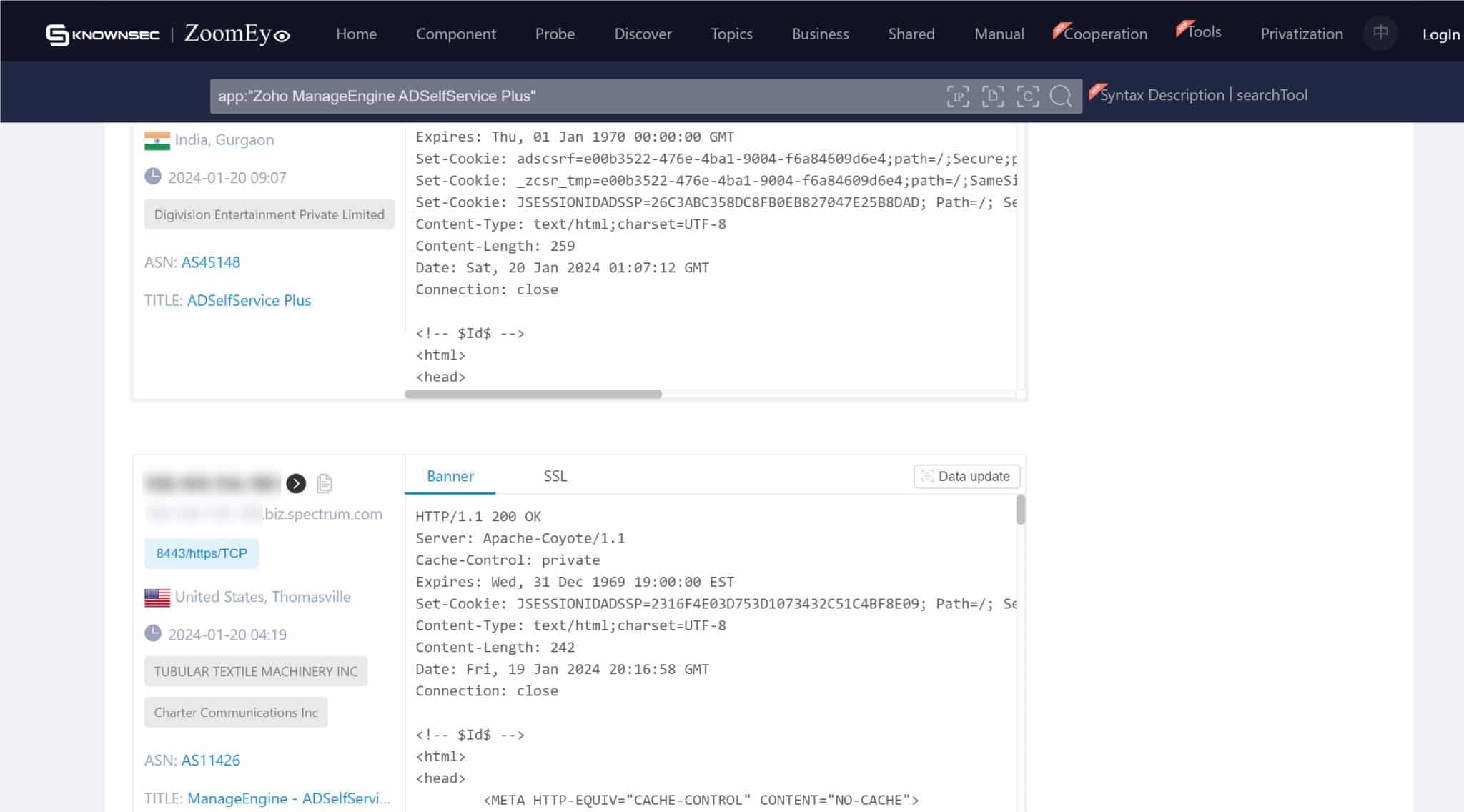
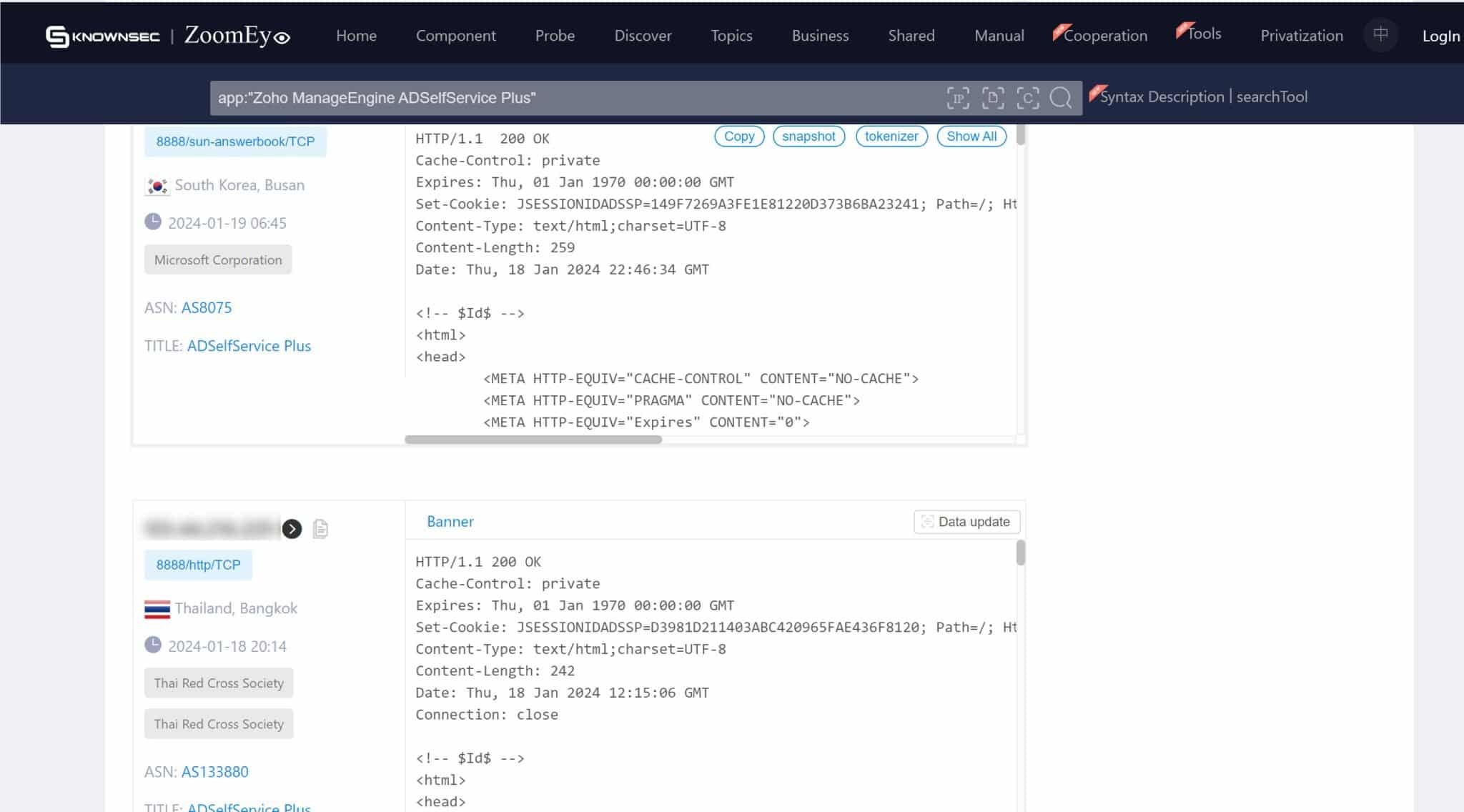
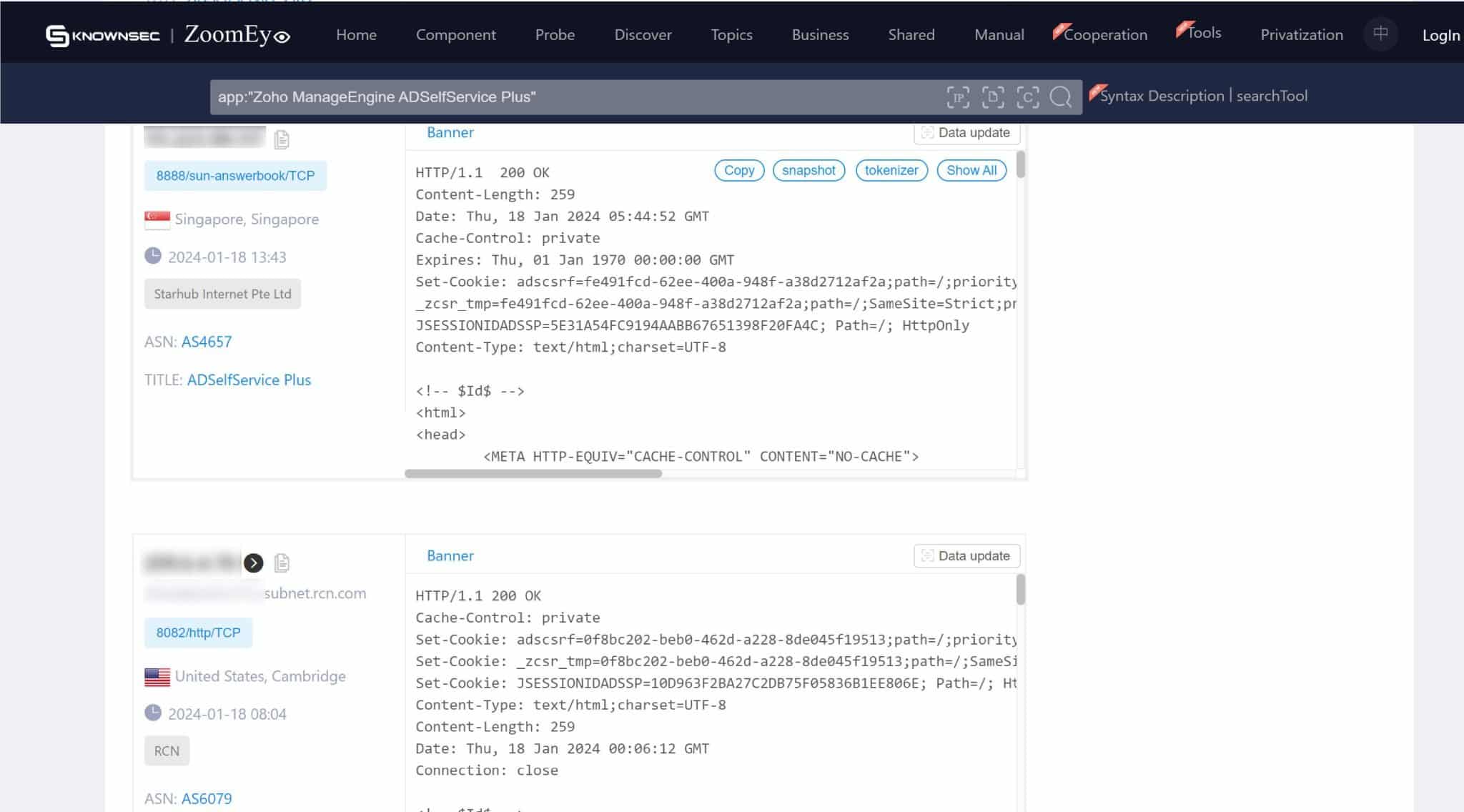
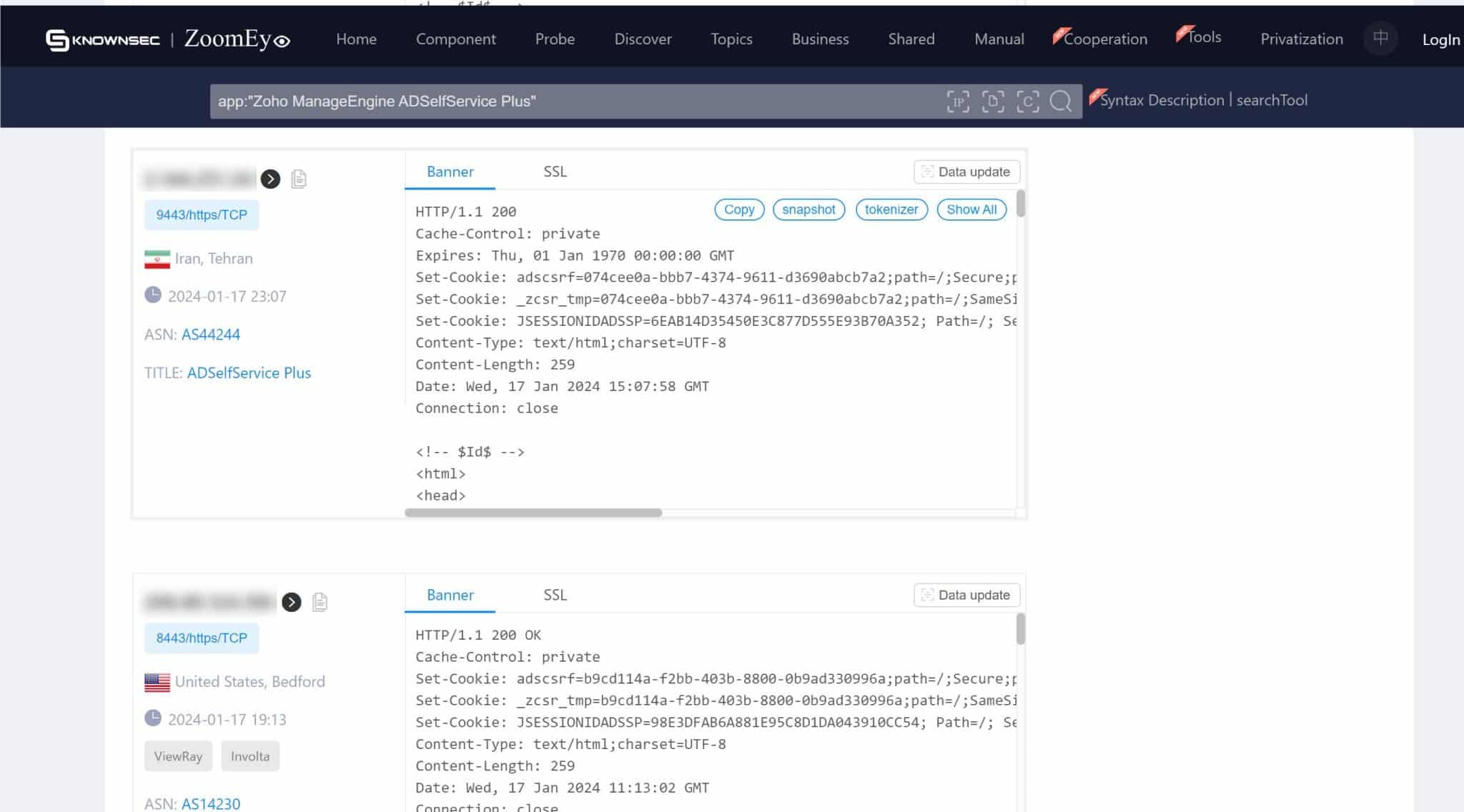
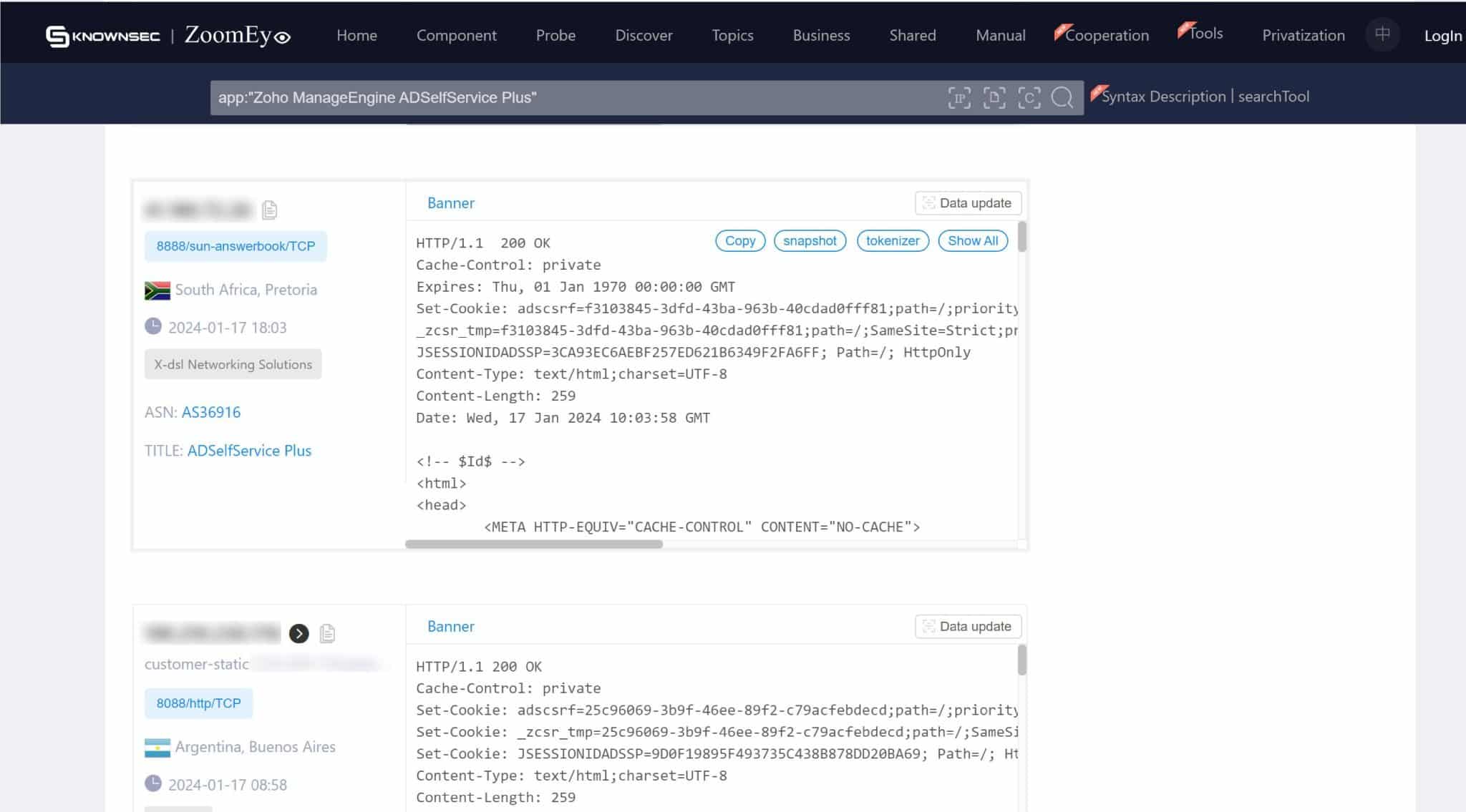
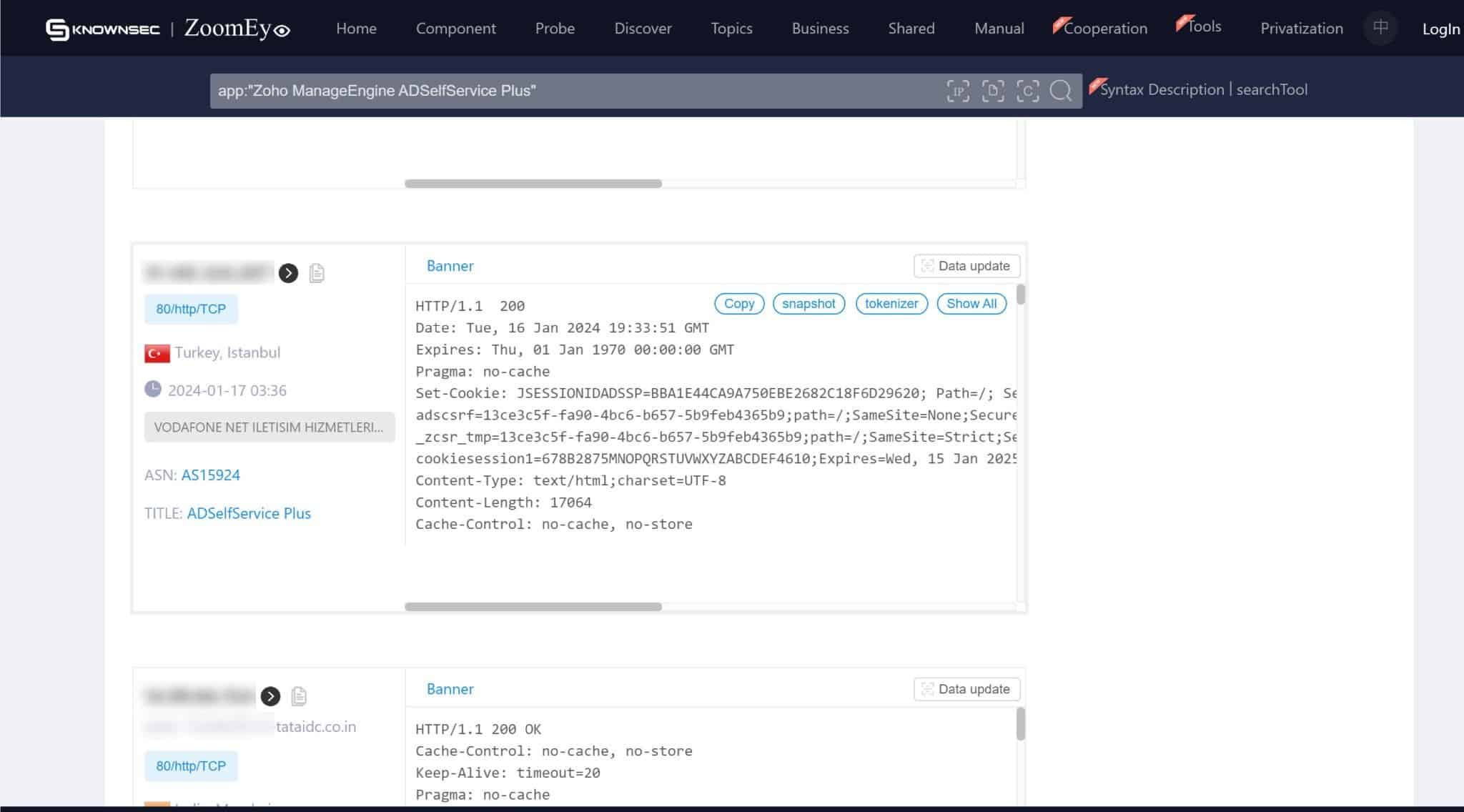
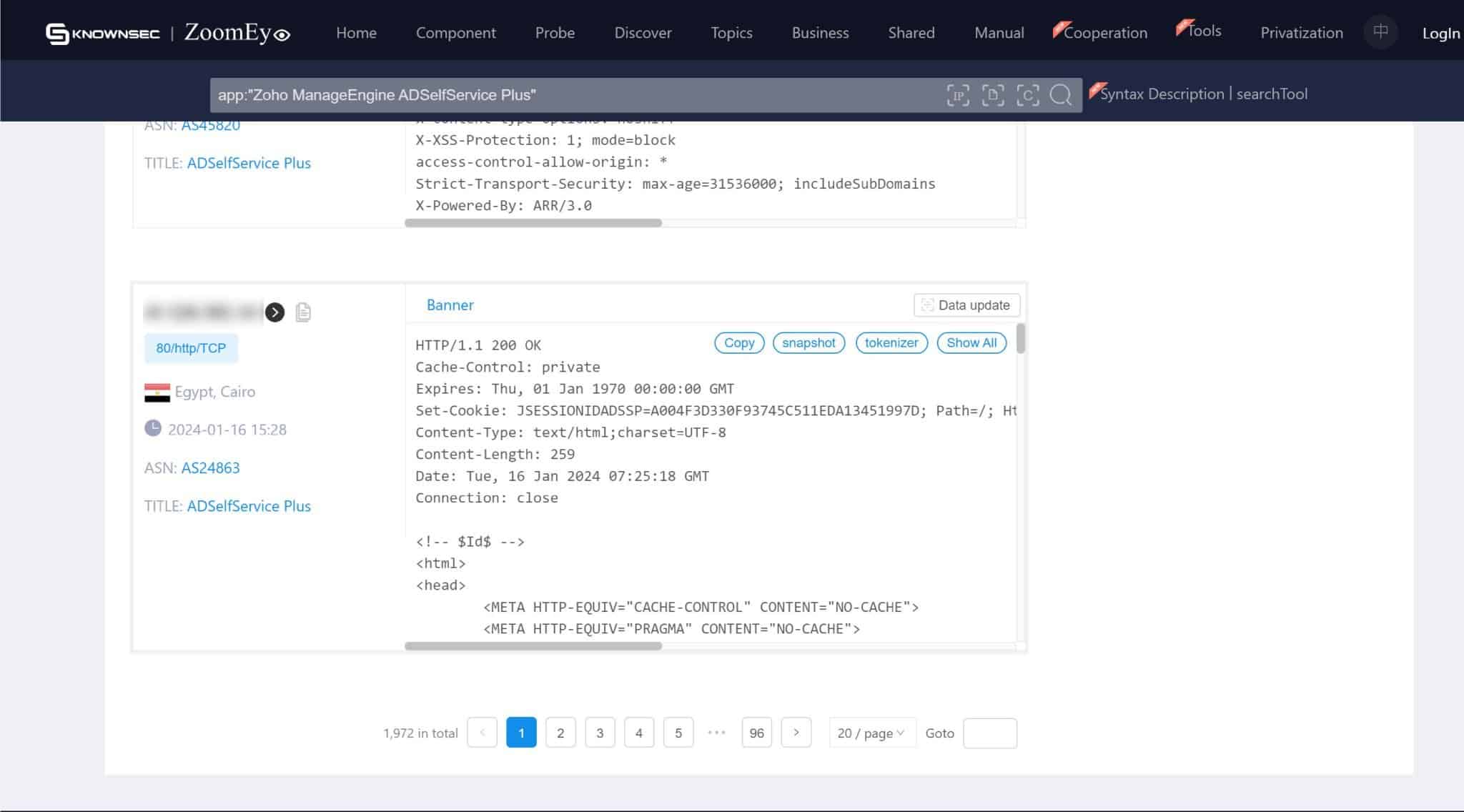
On the screenshots below, we can see numerous instances of servers exposed to ADSelfService. This exposure means that without the necessary remediation, these servers are susceptible to exploitation through CVE-2024-0252. The exact figures and locations of these vulnerable servers provide a tangible perspective on the potential reach of this security flaw.
Conclusion: Embracing Proactivity in Cybersecurity
2024’s emerging threats, such as CVE-2024-0252, are a reminder of the dynamic and challenging nature of cybersecurity. To navigate this landscape effectively, organizations must be disciplined, continuously monitoring their security controls and correlating them with intelligence feeds to stay ahead of potential threats. This integration is crucial for maintaining an accurate understanding of the security landscape and the in-house security configuration and ensuring that misconfigurations are met head-on to reach maximum effectiveness and adaptability to new challenges. The ultimate goal is to create a security posture that is not only reactive to exposures but also predictive and preventative. This involves a deep understanding of the organization’s security infrastructure, continuous optimization of security controls , and the ability to make data-driven security decisions.