Instantly remediate risks without disrupting operations
Use Veriti to proactively assess and safely remediate exposures across the entire security stack on-prem and in the cloud.
Challenge
Most security incidents are traced to misconfigured security controls.
Exposure Assessment Platform
Remediate your exposures in the cloud and on-prem
Neutralize threats
before they happen
Prioritize and address critical vulnerabilities using business context and available compensating controls to preemptively protect against attacks.

Correlate exposures to misconfigurations
Correlate insights across security layers to consistently uncover gaps in security controls, detect threats, identify vulnerabilities, and anticipate potential business disruptions.

Maintain Business
Continuity
Continuously analyze security logs for false positives before applying any remediation actions.
The only platform for safe exposure remediation.
38 Remediations
per session are performed every time users access Veriti
556 Non-disruptive remediations
handled on avg. per month
$220,000
Continuous Exposure Assessments
Aggregate and normalize
Veriti aggregates data from diverse security tools and threat intelligence sources, providing a unified view of all exposures across the environment. By normalizing and deduplicating this data, Veriti ensures consistent, accurate information for more effective exposure assessment.

Assess
Veriti assesses and correlates each exposure with configuration data, threat intelligence, and potential false positives to understand the potential impact on the organization.
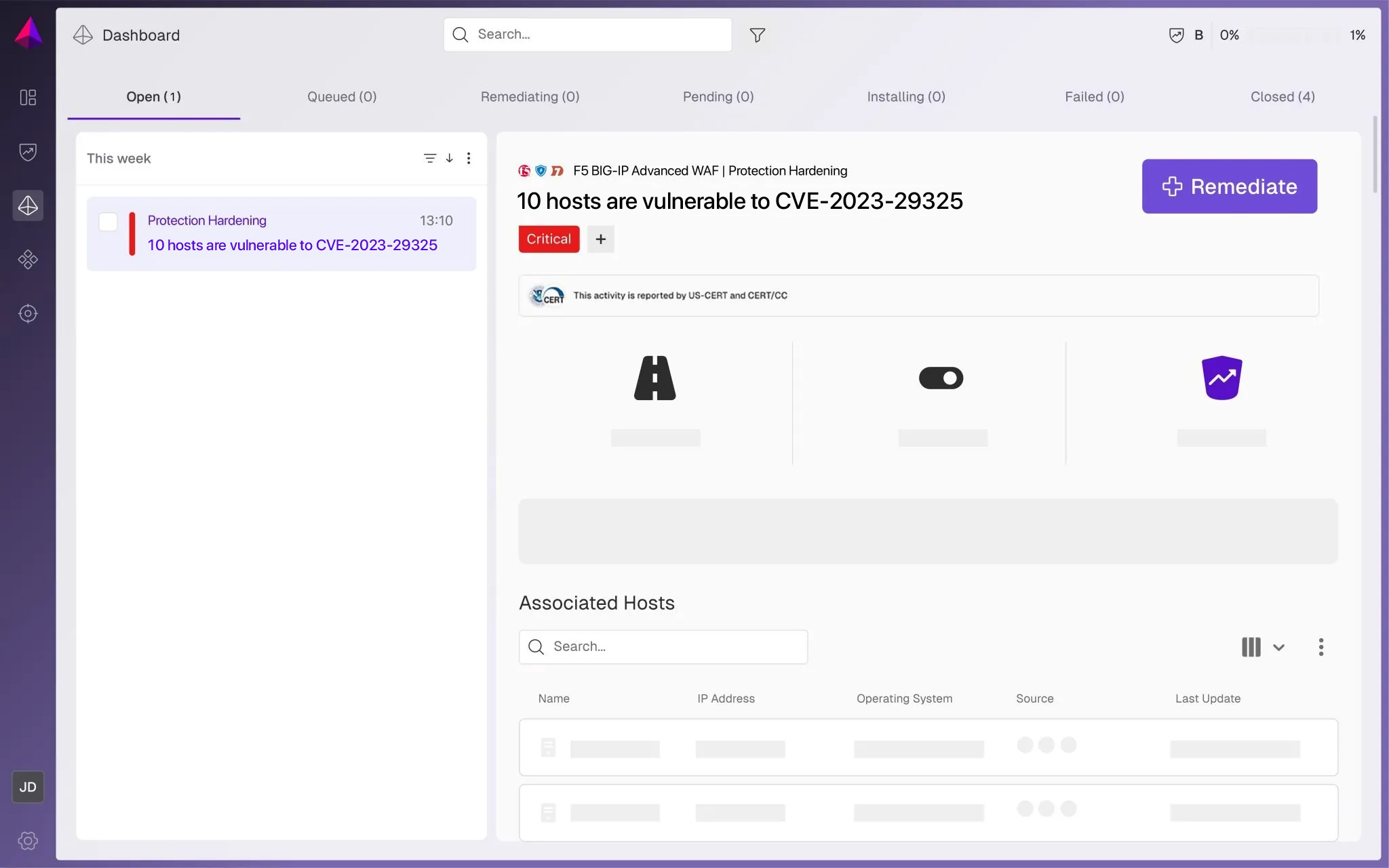
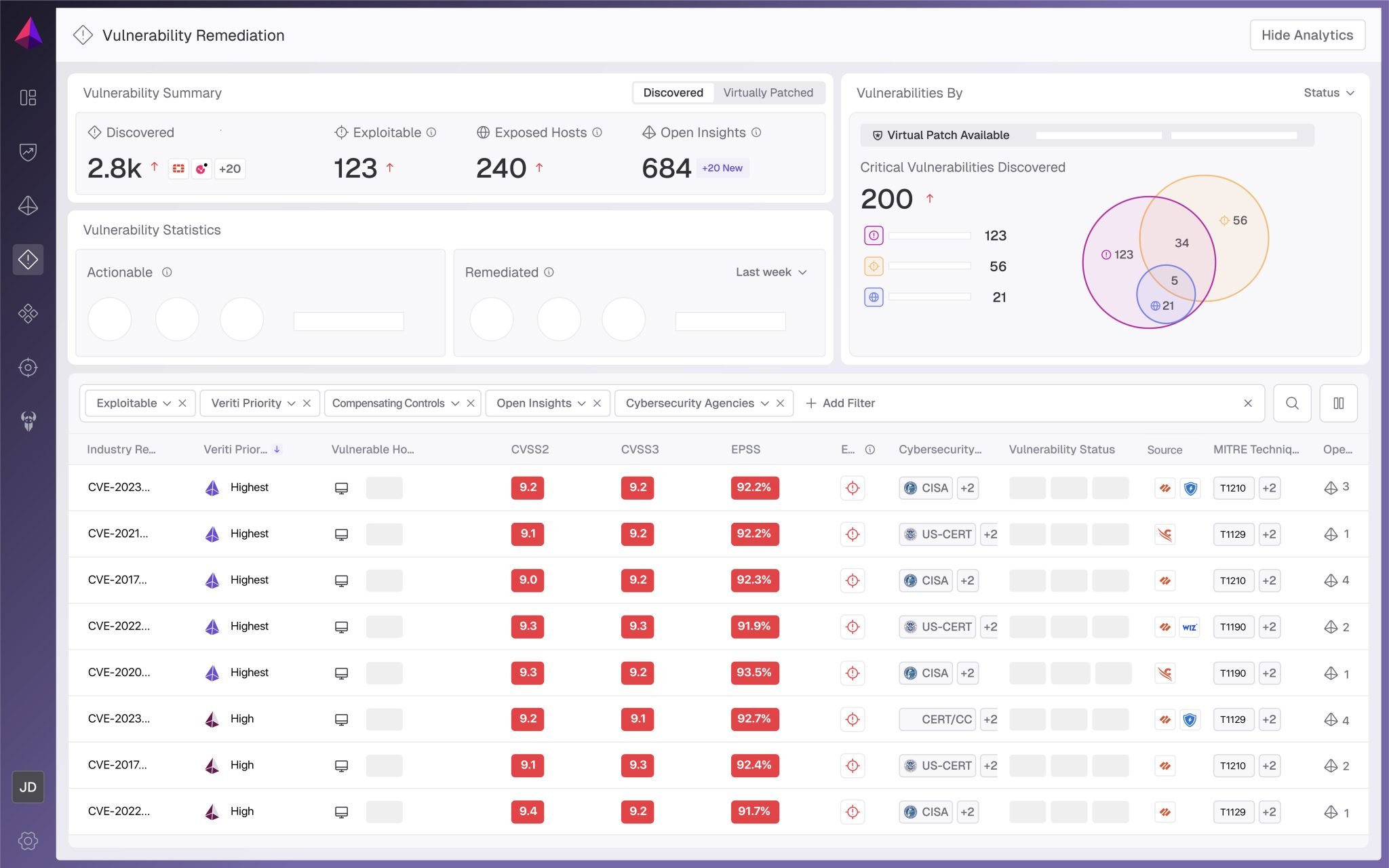
Prioritize
Veriti factors in the availability of compensating controls, business impact, and exploitability, allowing teams to address the highest-risk vulnerabilities first.
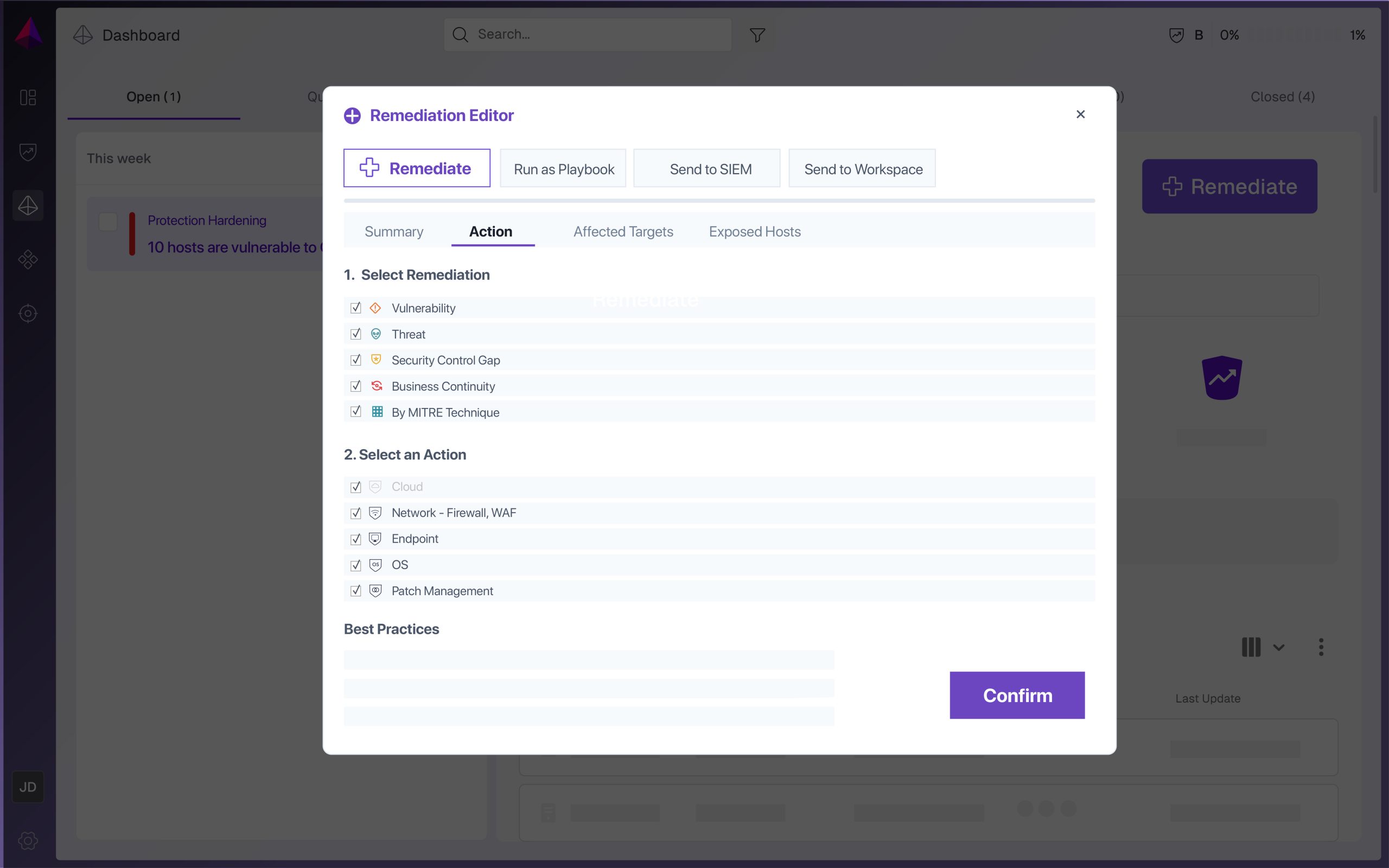
Remediate
Veriti facilitates a one-click safe remediation via direct configuration changes or by leveraging SIEM/SOAR playbooks and ITSM tools.




Veriti recognized as a Cool Vendor in the 2023 Gartner® Cool Vendors™ for Modern Security Operations Center report

Connect Everything, Fix Anything:
60+ Integrations with Veriti
Align all disparate cross-vendor security solutions, to a unified security posture management platform, including complete visibility to the entire security estate, mapping of all security assets, their preventative maintenance level and relevant vulnerabilities
“With Veriti we can ratchet up the security level using the existing tools, turning on features or increasing the stance while focusing on business continuity without disrupting anything within the organization.”

Eric Anderson
Cybersecurity Architect, Atlantic Data Security





